Audit in an Automated Environment – CA Inter Audit Questions bank is designed strictly as per the latest syllabus and exam pattern.
Audit in an Automated Environment – CA Inter Audit Question Bank
Question 1.
(e) The auditor should understand and consider the risks that may arise from the use of Information Technology (IT) Systems. (May 2018, 5 marks)
Answer:
The auditor should understand and consider the following risks that may arise from the use of information Technology (IT) Systems.
- Inaccurate Processing of data, processing inaccurate data, or both.
- Unauthorized access to data.
- Direct data changes (back-end changes)
- Excessive access I Privileged access (Superusers).
- Lack of adequate segregation of duties.
- Unauthorized changes to systems or programs.
- Failure to make necessary changes to systems or programs.
- Loss of data.
Question 2.
The auditor’s responsibility include reporting on Internal Financial Controls over Financial Reporting which include and understanding IT environment of the company and relevant risks and control. Mention any three situation where IT will be relevant to an audit. (Nov 2019, 3 marks)
Answer:
The auditor’s responsibility includes reporting on Internal financial controls over financial reporting which include an understanding IT environment of the company and relevant risks arid control. Following are some situations In which IT will be relevant to an audit.
- Increased use of systems and Application Software in Business (for example, use of ERPS)
- The complexity of transactions has increased (multiple systems, network of systems)
- Hi-tech nature of business (Telecom, e-commerce)
- The volume of transactions are high (Insurance, Banking, Railway ticketing).
- Company Policy (compliance).
- Regulatory requirements – Companies Act, 2013 IFC, IT Act, 2008.
- Required by Indian and International Standards- ISO, PCI – DSS, SA 315, SOC, ISAE.
Question 3.
Write short notes on Firewalls. (May 2008, 5 marks)
Answer:
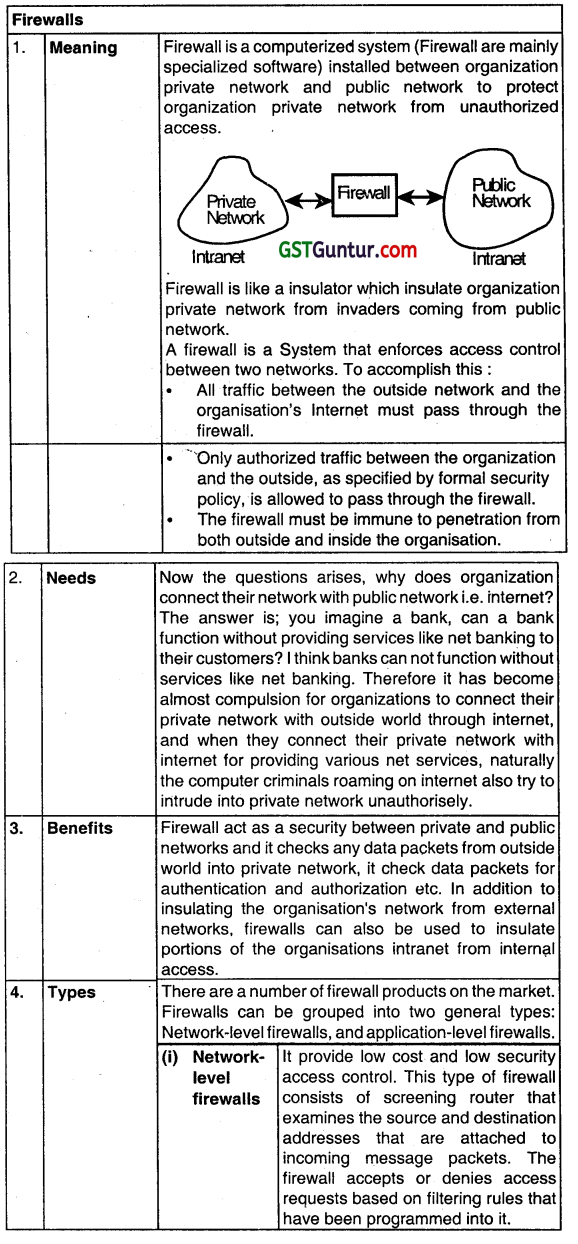
Question 4.
As an IS auditor, what are the risks reviewed by you relating to IT systems and processes as part of your functions? (Nov 2014, 4 marks)
Answer:
Risks to be reviewed relating to IT systems and processes as part of audit functions are as follows:
- It is required to check whether information security is adequate?
- Auditor review and check whether IT resources are efficiently utilized?
- Review and check IT-related frauds.
- Review and check whether organizations have adequate IT-related policies.
- Review and check whether system development and maintenance process‘s controllèd processes or not?
![]()
Question 5.
List any five points that an auditor should consider to obtain an understanding of the Company’s automated environment. (May 2018, 5 marks)
Answer:
Points that an auditor should consider to obtain an understanding of the company’s automated environment:
- Information systems being used (one or more application systems and what they are).
- Their purpose (financial and non-financial).
- Location of IT systems – local vs global.
- Architecture (desktop-based, client-server, web application, cloud-based)
- Version (functions and risks could vary in different versions of same application).
- Interfaces within systems (in case multiple systems exits).
- In-house vs packed.
- Outsourced activities (IT maintenance and support).
- Key persons (CIO, CISC, Administrators).
Question 6.
Analyse how risks in the IT system if not mitigated could have an impact on the audit. (Nov 2020, 3 marks)
Question 7.
Explain whether the following statements are correct or Incorrect, with reasons /explanations/examples:
The Complexity of a business environment depends on the level of automation i.e., it a business environment is more automated, It is likely to be less complex. (Jan 2021, 2 marks)
Question 8.
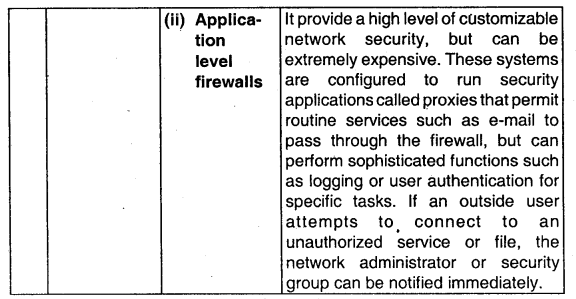
What is scope of output control of an application system? Suggest various types of output controls which are enforced (or confidentiality, integrity, and consistency of output. (2013 – May 6 marks)
Answer:
The scope of output controls of an application system is to provide functions that determine the data content availability to users, data, format, timeliness of data and how data is prepared and routed to users.
Question 9.
Write short note on Effect of Computers on Evidence Collection for audit. (May 2015, 4 marks)
OR
The advent of computer has drastically transformed the mode of evidence collection by an auditor. Discuss the various issues involved in the performance of evidence collection and understanding the reliability of controls. (May 2016, 6 marks)
Answer:
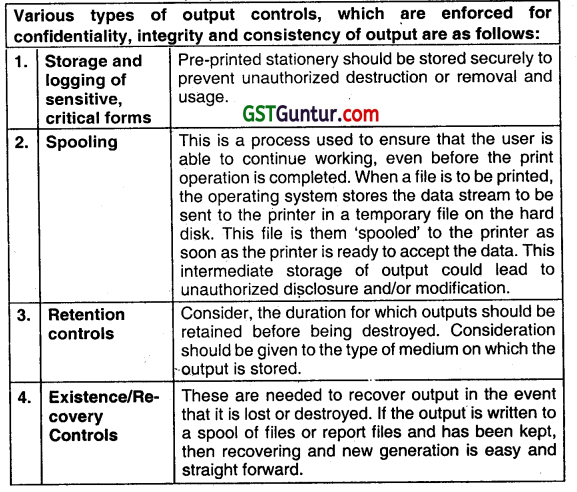
- Effect of Computers on Evidence Collection for Audit
- Evidence collection for Audit by computers have following effects:
- Data Retention and Storage
- A client’s storage capabilities may restrict the amount of historical data that can be retained online. Insufficient data retention capacities make unable the auditor to review whole required transactions.
2. Audit Evidence
Certain transactions may be generated automatically by the computer system in which formal transaction authorization may not have been explicitly provided.
3. Lack of Visible Output
The results of transaction processing may not produce hard copy form of output i.e. printouts.
4. Lack of Visible Audit Trail
The audit trails in some computer systems may exist for only a short period of time. It makes auditor’s job very difficult.
5. Absence of Input Documents
Transaction data may be entered Into the computer directly without the presence of supporting documentation.
6. Legal Issues
The use of computers are in increasing trend Both public and private sector intend to make use of and electronic trading over the Internet.
Question 10.
Examine with reason (in short) whether the following statement is correct or incorrect:
When auditing in an automated environment, inquiry is often the most efficient and effective audit testing method. (Nov 2018, 2 marks)
Answer:
Incorrect:
When auditing in an automated environment, inquiry is often the most efficient audit testing method but less effective. Moreover, testing through inquiry alone is not sufficient. Inquiry should be corroborated by applying any one or a combination of observation, inspection, or reperformance.
![]()
Question 11.
Discuss the common methods applied by the auditor when testing in an automated environment is done by him. (Jan 2021, 4 marks)
Question 12.
Why are computer-assisted audit techniques (CAAT) needed in a Computer Information Systems (CIS) environment and how It helps the auditor In obtaining and evaluating audit evidences? (Nov 2007, 6 marks)
OR
What is CAATS? Why are CAAT required in Coniputerised information system (CIS) environment? (Nov 2011, 8 marks)
Answer:
CAAT In EDP Audit: The use of computers may result in the design of systems that provide less visible evidence than those using manual procedures. Also, many persons may access these systems. System characteristics resulting from the nature of EDP processing that demand the use of Computer Aided Audit Techniques:
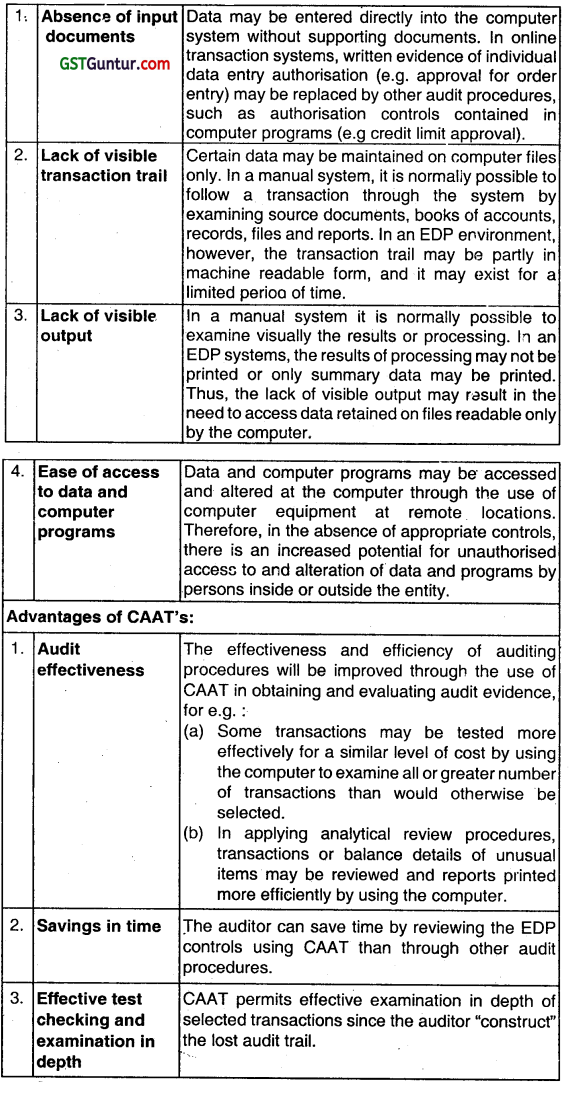
Question 13.
Discuss the following:
With respect to audit in an automated environment, explain the following:
(i) CAATs
(ii) Data Analytics
(iii) Database
(iv) Information Systems
(v) Privileged access (Nov 2018, 5 marks)
Answer:
(i) CAATs:
CAATs, shorter form of Computer Assisted Audit Techniques, are a collecton of computer-based tools and techniques that are used in an audit for analysing data in electronic form to obtain audit evidence.
(ii) Data Analytics:
Data Analytics is a combination of processes, tools and techniques that are used to tap vast amounts of electronic data using information systems.
(iii) Database:
Database is a logical subsystem within a larger information system where electronic data is stored in a predefined form and retrieved for use.
(iv) Information Systems:
Information Systems refers to a collection of electronic hardware, software, networks, and processes that are used in a business to carry out operations and transactions.
(v) Privileged Assess:
It is a type of super user access to information systems that enforces less or no limits on using that system.
Question 14.
While it is true that companies can benefit immensely from the use of data analysis items of increased profitability, better customer service, etc.,. Analyse various functions that can be performed even by the auditor also using Data Analytics tools and techniques in the audit process to obtain good results. (Nov 2020, 4 marks)
Multiple Choice Question
Question 1.
……………. basically refer’s to a business environment where the processes, operations, accounting and even decisions are carried out by using computer systems.
(a) Business Environment
(b) Computer Environment
(c) System Environment
(d) Automated Environment
Answer:
(d) Automated Environment
Question 2.
Automated Environment is also known as
(a) Information Systems
(b) Information Technology System
(c) Automated Technology System
(d) (a) or (b)
Answer:
(d) (a) or (b)
![]()
Question 3.
The fundamental principle of an automated environment is the ability to carry out business with
(a) manual intervention and system driven
(b) less manual intervention and less system driven
(c) less system-driven and more manual intervention
(d) less manual intervention and more system driven
Answer:
(d) less manual intervention and more system driven
Question 4.
Complexity of a business environment is ……………….. related with Automated Environment.
(a) Directly
(b) Indirectly
(c) Independently
(d) None
Answer:
(a) Directly
Question 5.
Benefits of automated environment except.
(a) Enable faster business operations
(b) Ability to process large volumes of transactions
(c) More proof to human errors
(d) Integration between business operations
Answer:
(c) More proof to human errors
Question 6.
As the complexity, automation and dependence of business operations on IT systems increases, the severity and impact of IT risk ………………. accordingly.
(a) decreases
(b) increases
(c) sustain
(d) adjusted
Answer:
(b) increases
Question 7.
For audit of financial statements auditor ………………… understand the IT system and its relevance
(a) should not
(b) should
(c) may
(d) not necessary to
Answer:
(b) should
Question 8.
With the introduction of ……………. there is greater emphasis given to Internal financial control (IFC) from a regulatory point of view
(a) CAAR 2014
(b) SEBI Regulation
(c) Standard of Auditing
(d) Companies Act 2013
Answer:
(d) Companies Act 2013
![]()
Question 9.
Who is responsible for the implementation of internal control framework within the company?
(a) Directors
(b) TCWG
(c) Auditor
(d) Directors and TCWG
Answer:
(d) Directors and TCWG
Question 10.
Situation in which IT will be not relevant for an audit
(a) Complexity of transactions has increased
(b) Regulatory requirements Companies Act 2013, IFC, IT Act 2008
(c) Decreases efficiency and effectiveness of audit
(d) Volume of Transactions are high
Answer:
(c) Decreases efficiency and effectiveness of audit
Question 11.
IT can be relevant to Audit is by using using computer-assisted audit techniques (CAAT)
(a) Data System technique
(b) Data Statistics
(c) Data Analytics
(d) Data Analysis
Answer:
(c) Data Analytics
Question 12.
Understanding of a company’s IT environment that is obtained should be documented as per
(a) SA-200
(b) SA-210
(c) SA-215
(d) SA -230
Answer:
(d) SA -230
Question 13.
Impact on substantive Audit due to IT-related risks except
(a) cannot rely on the data obtained from system
(b) cannot rely on IT-dependent manual controls
(c) more audit evidence is needed
(d) system data and reports should be tested substantively for completeness and accuracy.
Answer:
(b) cannot rely on IT-dependent manual controls
Question 14.
Which of the following is a General IT control?
(a) IT Environment
(b) Application Control
(c) Access Security
(d) IT Dependent Control
Answer:
(c) Access Security
Question 15.
Which of the following es an automated control?
(a) System Generated Report
(b) Configuration
(c) Program Change
(d) Application Control
Answer:
(b) Configuration
![]()
Question 16.
Which is not a type of control in automated environment.
(a) General IT control
(b) Application control
(c) IT-Dependent Control
(d) Entity-level control
Answer:
(d) Entity-level control
Question 17.
……………….. are policies and procedures that relate to many applications and support the effective functioning of application control
(a) General IT control
(b) Application control
(c) IT Dependent control
(d) None of the above
Answer:
(a) General IT control
Question 18.
General IT controls are apply to, except
(a) mainframe
(b) mini frame
(c) maga frame
(d) end-user environment
Answer:
(c) maga frame
Question 19.
General IT control is also known as
(a) Direct control
(b) InDirectcontrol
(c) Pervasive control
(d) (b) or (c)
Answer:
(d) (b) or (c)
Question 20.
Application controls include …………………… that operate at a business process level.
(a) automated controls
(b) manual controls
(c) IT controls
(d) both automated or manual controls.
Answer:
(d) both automated or manual controls.
Question 21.
Automated application controls are embedded into IT applications which helps in ensuring the ………………….. of date In those systems.
(a) completeness
(b) accuracy
(c) integrity
(d) all of these.
Answer:
(d) all of these.
Question 22.
General IT Controls and Application controls over IT systems are ………………… .
(a) interrelation
(b) independent
(c) dependent
(d) intra related
Answer:
(a) interrelation
![]()
Question 23.
Testing in automated environment, which method is commonly used
(a) Inspect the configuration defined in an application
(b) Observe how a user processes transactions under different scenarios
(c) Obtain an understanding of how an automated transaction is processed by doing a walk through one end-to-end transaction using a combination of inquiry, observation, and inspection
(d) Any of the above mode
Answer:
(d) Any of the above mode
Question 24.
Internal Financial Controls refers to the policies and procedures put in place by companies for ensuring.
(a) reliability of financial reporting
(b) compliance with applicable laws and regulations
(c) prevention and detection of frauds and safeguarding of assets
(d) All of the above conditions
Answer:
(d) All of the above conditions
Question 25.
………………. has placed a greater emphasis on the effective implementation and reporting on internal controls for a company
(a) Companies Act 2013
(b) CAAR, 2014
(c) SEBI 1992
(d) Companies Rules 2017
Answer:
(a) Companies Act 2013
Question 26.
Auditor’s opinion on Internal Financial Controls (IFC) is applicable for a listed companies from the financial year
(a) 2013-2014 onwards
(b) 2014-2015 onwards
(c) 2015-2016 onwards
(d) 2016-2017 onwards
Answer:
(b) 2014-2015 onwards
Question 27.
The ………………… have primary responsibility of implementing and maintaining and effective internal controls framework.
(a) Statuary auditors
(b) Directors
(c) Management
(d) Directors and management
Answer:
(d) Directors and management
Question 28.
Who is responsible for evaluation, validation, and reporting on the designing and operating effectiveness of internal financial control
(a) Statutory auditors
(b) Internal auditors
(c) Directors
(d) Management
Answer:
(a) Statutory auditors
Question 29.
Control based audit approach excludes
(a) Risk assessment
(b) Audit Programme
(c) Understand and Evaluation
(d) Test for Operating Effectiveness
Answer:
(b) Audit Programme
![]()
Question 30.
Risk assessment under controls based audit approach include
(a) Qualitative and Quantitative Consideration
(b) Relevant Financial Statement Assertions (FSA)
(c) Identify likely sources of misstatement
(d) All of the above
Answer:
(d) All of the above
Question 31.
Understand and evaluating under control based audit approach excludes
(a) Document understanding of business processes using flow charts/Narrative.
(b) Prepare Risk and Control Matrices (RCM)
(c) Relevant Financial Statement Assertions (FSA)
(d) IT General Controls, Application Controls
Answer:
(c) Relevant Financial Statement Assertions (FSA)
Question 32.
Reporting under controls based audit approach excludes
(a) Evaluate Control Deficiencies
(b) Prepare Risk and Control Matrices (RCM)
(c) Internal Controls Memo (1CM)
(d) AudItor’s report
Answer:
(b) Prepare Risk and Control Matrices (RCM)
Question 33.
A combination of processes, tools and techniques that are used to tap vast amounts of electronic data to obtain meaningful information is called ………………….. .
(a) data statistic
(b) data science
(c) data analytics
(d) data analysis
Answer:
(c) data analytics
Question 34.
The tools and techniques that auditors use in applying the principles of data analytics are known as
(a) Computer Aided Auditing Techniques
(b) Computer Assisted Auditing Techniques
(c) Computensed Audit Assisted Technique
(d) Computerised Aided Audit Technique
Answer:
(b) Computer Assisted Auditing Techniques
Question 35.
Data analytics can be used In
(a) testing of accounting records
(b) testing of electronic records
(c) data residing in IT system
(d) (b) and (c) both
Answer:
(d) (b) and (c) both
![]()
Question 36.
………………… refers to the digital content that is stored in electronic form with computer system
(a) Data
(b) Data Science
(c) Data Analysis
(d) Data Analysis
Answer:
(a) Data
Question 37.
A logical subsystem within a large information system where electronic data in stored in a predefined from and retrieved for use, is known as:
(a) Data
(b) Database
(c) Data Analysis
(d) Data Analytics
Answer:
(b) Database
Question 38.
A type of super user access to information system that enforces less or no limits on using that system, is known as:
(a) Risk assessment
(b) Risk evaluation
(c) Privileged access
(d) None of them
Answer:
(c) Privileged access