CA Inter EIS SM Case Studies – CA Inter EIS SM Notes is designed strictly as per the latest syllabus and exam pattern.
CA Inter EIS SM Case Studies – CA Inter EIS SM Study Material
Integrated Case Studies
Case Study 1
Monty da dhaba is a small local suburban restaurant yet a very well known due to its quality of food, services and pocket friendly prices. It commenced its services in January, 2020. With a limited team of 8 people and a small space they were doing well to start with. They had picked up really well despite of using the traditional ways of serving like either dine in and take away from the outlet.
Due to limited staff and a small team their delivery reach was not functional. Also due to space limitation the restaurant was always full with minimum half hour waiting time. Due to which people often switched to available options in the area around. Therefore despite of tasty and budget friendly food they were not able to expand its base nor grow as much as their competitors.
One of their loyal customers who was also a consultant reached out to the owner and explained him how he could just stick to making good and tasty food availability and also expand its customers base by outsourcing delivery and tying with food apps. He introduced him to the concept of Business Process Automation (BPA) by explaining him its advantages and also helping him with smooth implementation of BPA.
Based on the above case scenario, answer the following questions:
Question 1.
Entity must need these:
(a) Specific
(b) Measurable
(c) Attainable
(d) Relevant
Answer:
(d) Relevant
![]()
Question 2.
Which one of the following is not a benefit of Business Process Automation?
(a) Reduce turnaround time
(b) Improved Operational efficiency
(c) Structured
(d) Reduce costs
Answer:
(c) Structured
Question 3.
What are the factors affecting success of BPA?
(a) Confidentiality
(b) Integrity
(c) Availability
(d) All of the above
Answer:
(d) All of the above
Question 4.
They deal with the core business and value chain.
(a) Primary Process
(b) Secondary Process
(c) Management Process
(d) Business Process Automation
Answer:
(a) Primary Process
Question 5.
It ensures that data is available when asked for:
(a) Confidentiality
(b) Integrity
(c) Availability
(d) Timeliness
Answer:
(d) Timeliness
![]()
Question 6.
Which one of the following is not a step to go about implementing Business process Automation
(a) Define why we plan to implement a Business Process Automation (BPA)?
(b) Define the objectives/goals to be achieved by implementing BPA
(c) Calculate the RoI for project
(d) Calculate IRR of the Project
Answer:
(d) Calculate IRR of the Project
Case Study 2
H Parampara Ltd. is a sub-broking firm established in early 80’s with 4 partners who are now in their late 60’s and 70’s. It has a loyal customer base and is high on values and integrity but has a traditional approach of working.
With the new line of partners stepping in, their goal is to not only survive the competition but also maintain the legacy of the firm but there is a serious concern it needs to address first. The firm believes the primary concern that needs to be addressed on priority is identifying and analyzing the risk faced by the firm considering that the firm prefers working traditionally and has an outdated technology and the way the data is handled and managed manually.
The partners of the firm have unanimously hired you to identify and analyse high level of risk exposure and come up with a risk management strategy to manage the risk faced by the firm.
Based on the above case scenario, answer the following questions:
Question 1.
Which is the type of risk that will expose Parampara Ltd. to fines & penalties from a regulatory agency?
(a) Strategic
(b) Financial
(c) Reputational
(d) Regulatory
Answer:
(d) Regulatory
Question 2.
The most important step in risk management process is:
(a) Understand Threat and Vulnerabilities
(b) To eliminate the risk
(c) to identify the sources of risk, the areas from where risks can occur
(d) To implement controls
Answer:
(c) to identify the sources of risk, the areas from where risks can occur
![]()
Question 3.
Risk that could result in a negative financial impact to the organization (waste or loss of assets)
(a) Strategic
(b) Financial
(c) Reputational
(d) Regulatory
Answer:
(b) Financial
Question 4.
“Technology keeps on evolving and changing constantly and becomes obsolete very quickly.” This statement belongs to:
(a) New social engineering techniques employed to acquire confidential credentials
(b) Dependence on vendors due to outsourcing of Technology services
(c) Vendor related concentration risk
(d) Segregation of Duties (SoD)
Answer:
(b) Dependence on vendors due to outsourcing of Technology services
Question 5.
____________ is the weakness in the system safeguards.
(a) Threat
(b) Exposure
(c) Vulnerability
(d) Counter Measure
Answer:
(c) Vulnerability
Case Study 3
As a Database Administrator, you are invited in a Conference to speak on Data Types in front of audience of aspiring CA Students. You decide to segment your lecture in following parts:
- Master Data & Non-Master Data and Identify the types of Master Data in Financial & Accounting Systems.
- Voucher, different types of voucher and the peculiarities that must be considered while allotting a voucher number to a voucher.
Post conference, you were hired as a Consultant by a TOP CA Firm to manage the IT Infrastructure. You noticed that the CA firm was having installed applications in their computer systems, and as per the immense work load Cloud Applications would be much better. You discussed the Advantages and disadvantages of both the applications.
And since many departments in the CA firm were following Non-Integrated system, you also discussed the features of Integrated ERP System and Non-Integrated System with the Management of the CA firm.
Based on the above case scenario, answer the following questions:
Question 1.
What is not a part of Inventory Master Data?
(a) Stock Item
(b) Stock Group
(c) Salary Structure
(d) Godowns
Answer:
(c) Salary Structure
![]()
Question 2.
Which of the following is a main characteristic of ERP System?
(a) Separate data maintenance by each department
(b) Centralised Database
(c) No direct inter-department communication
(d) None of the above
Answer:
(b) Centralised Database
Question 3.
If an organization does not want to install Financial Application on its own System, they can use ___________ Applications.
(a) Cloud-based
(b) Web
(c) Installed
(d) Mobile
Answer:
(a) Cloud-based
Question 4.
At the work place, an employee wants to maintain a record of physical receipts of goods purchased from a vendor in his Accounting System. Which Voucher type shall he use?
(a) Delivery note
(b) Receipt note
(c) Sales
(d) Purchase
Answer:
(b) Receipt note
Question 5.
Which of the following transactions are not recorded in the Voucher Type “Contra” of the Accounting System?
(a) Cash deposit in bank
(b) Cash withdrawal in bank
(c) Cash transfer from one location to another
(d) Recording of all types of trading sales by any mode
Answer:
(d) Recording of all types of trading sales by any mode
![]()
Question 6.
Non-master includes….
(a) Debit ledger name
(b) Voucher number
(c) Credit ledger name
(d) None of the above
Answer:
(b) Voucher number
Questions 7.
_________ is a documentary evidence of a non-cash/bank transaction.
(a) Receipt
(b) Journal
(c) Debit Note
(d) Memorandum
Answer:
(b) Journal
Case Study 4
Sweet & Sour is an established food chain with five branches at different locations within Delhi. In 2018, the management decided to start a tiffin services with 24×7 availability on regular basis. To do so, they decided to acquire a software which would be an online assistant to its customers by providing them a complete detail about their services. The Management asked its manager to present them a report mentioning the benefits, risks, control objectives and above all highlighting any changes that are required in the working of food chain.
The management settled on a plan to benefit all its customers by providing them discounted coupons in case they recommend their services to others and customer ensuring to provide the food chain of three new customers. Also, the management decided for a centralized billing system that mandatorily requires customer’s name and phone number to be filled for each bill that system generates. To maintain these necessary details of its customers, the data management team of Sweet & Sour implemented major changes in the database design of its billing software, Subsequently, the security and database maintenance has become essential to protect the system against any unlawful activity as the database now contains the personal details of its customers.
Based on the above case scenario, answer the following questions:
Question 1.
The software which food chain decided to buy, to help their customer and provide them online help, falls under which of the following technology?
(a) Artificial Intelligence
(b) Data Mining
(c) Cloud Computing
(d) Mobile Computing
Answer:
(a) Artificial Intelligence
![]()
Question 2.
The Manager of the food chain prepared a document wherein he depicted various business processes of the food chain in diagrammatic form. Which of the following diagram will he use to present pre-defined process?
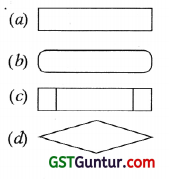
Answer:
(c)
Question 3.
The data management team of Sweet & Sour food chain was working to implement changes in database design of its billing software. Which of the following person will carry out routine data maintenance and monitor this task?
(a) Database Administrator
(b) Database Architect
(c) Database Analyst
(d) Database Advisor
Answer:
(c) Database Analyst
Question 4.
The management of Sweet & Sour has shown its concern what would happen if any of its employees dishonestly make use of personal information of customer. Which of the following IT Act, 2000 will help Sweet & Sour to deal with this situation?
(a) Section 43A
(b) Section 43
(c) Section 66E
(d) Section 66B
Answer:
(a) Section 43A
Case Study 5
A Cooperative society in Ghaziabad decides to open a bank named ABC Bank with its two branches located in Noida, Uttar Pradesh. The branches of banks are proposed to be connected to each other and all the processing and transactions being computerized with a centralized database. Further, to avoid manual working and proceed with advance technology, and at the same time to enhance functionality within branch; all the computer systems within all the departments in each branch would have connection-oriented network. The bank proposes to abide by all the regulations and compliance prevailing in India with respect to banking sector.
Mr. A is appointed as an IT – Head to carry out the Feasibility study of the proposed system and submit the report to top management of the Cooperative Society. After the report is submitted to the Top Management, following issues are raised by the management:
- There may be a conflict for some common resources in the network.
- Since the data is centrally located, it may create a possibility of access to non-relevant data by other departments.
- What would happen, if any employee intentionally destroys or alters the information residing in any of computer of any branch?
- Network security related issues between both branches of bank.
Based on the above case scenario, answer the following questions:
Question 1.
In purview of above case, under which legal provision of IT Act, 2000; the management can prove an employee guilty if (s) he intentionally destroys or alters the information residing in a computer resource of a branch?
(a) Section 43
(b) Section 65
(c) Section 66E
(d) Section 66C
Answer:
(a) Section 43
![]()
Question 2.
Which of the following control shall be implemented in both the branches of ABC bank to suppress the risk of possibility of access to non-relevant data by other departments?
(a) Proper training of the users with well documented manuals.
(b) Clear defining of change control procedures and holding everyone to them.
(c) Back up arrangement needs to be very strong.
(d) Access rights need to be defined very carefully and to be given on “Need to know” and “Need to do” basis only.
Answer:
(d) Access rights need to be defined very carefully and to be given on “Need to know” and “Need to do” basis only.
Question 3.
The feature of Internet banking through ABC Banks’ website allows ease and convenience to its customers. Which of the following is not the limitation of Internet banking?
(a) Difficult for a non-technical person
(b) Risk of data theft
(c) Written Record not to be maintained
(d) Overspending
Answer:
(c) Written Record not to be maintained
Question 4.
The Top management of cooperative society raised its concern over an issue related to conflict of sharing of common resources in network between its two branches. Select the terminology referring to the above concern.
(a) Resilience
(b) Contention
(c) Bandwidth
(d) Routing
Answer:
(b) Contention
Question 5.
In both branches of ABC bank, all the fixed asset acquisitions will be recorded as the control objective related to certain risk. Under which category this control objective falls?
(a) Configuration general ledger
(b) Transaction Fixed asset
(c) Master fixed asset
(d) Transaction general ledger
Answer:
(b) Transaction Fixed asset
![]()
Case Study 6
Limit limited was worried with respect to the Control of the Information System of its Organization. He and his employees were not aware of the Controls an Organization must have with respect to Environment, Physical Access, Logical Access, Managerial, etc.
You were hired as an Consultant to advise them regarding the basic purpose of information system controls in an organization. To explain how this is achieved by designing and effective information control framework, which comprise policies, procedures, practices, and organization structure, which gives reasonable assurances that the business objectives will be achieved.
You being an Consultant, also pointed out that Internal controls can be classified into various categories to illustrate the interaction of various groups in the enterprise and their effect on information systems on different basis.
Accordingly, your work should also include that controls are classified based on the time when they act, relative to a security incident; how important is having Physical security mechanisms in an organization provides protection to people, data, equipment, systems, facilities and company assets.
Based on the above case scenario, answer the following questions:
Question 1.
Classification of information systems controls based on objective of controls is:
(a) Environmental
(b) Detective
(c) Physical access
(d) Logical access
Answer:
(b) Detective
Question 2.
Classification of Information Systems Controls which is not based on Nature of IS Resource:
(a) Environmental
(b) Physical Access
(c) Managerial
(d) Logical Access
Answer:
(c) Managerial
![]()
Question 3.
Which of the following is an example of preventive control?
(a) Cash counts
(b) Bank reconciliation
(c) Documentation
(d) Rerun procedures
Answer:
(c) Documentation
Question 4.
This type of Lock are used in low security situations or when many entrances and exits must be usable all the time:
(a) Bolting Door Locks
(b) Electronic Door Locks
(c) Cipher locks
(d) None of the above
Answer:
(c) Cipher locks
Question 5.
These systems encompass a pair of doors that are typically found in entries to facilities such as computer rooms and document stations:
(a) Alive Man Doors
(b) Dead Man Doors
(c) One Man Door
(d) Three step door
Answer:
(b) Dead Man Doors
Case Study 7
The Chief Minister Office of a State Mr A plans to establish specific infrastructure setup with its access shared amongst members of the group constituting of some selected high-profiled dignitaries and officers from different ministries. The objective of the group is to carry out certain assignments related to security and integrity.
Mr A, himself, is using Google Apps through which he can access any application, service and data storage facilities on the Internet and pay as-per-usage.
Mr A has set up a XYZ university which wants to conduct online exams for its different courses for which a contract is given to vendor Mr. Z. The vendor provides computing resources such as processing power, memory, storage, and networks to the university users to run their online exam application on-demand.
Based on the above case scenario, answer the following questions:
Question 1.
Mr. A for the Chief Minister office and the members of the group is preferring to use which type of Cloud?
(a) Private
(b) Public
(c) Community
(d) Hybrid
Answer:
(c) Community
![]()
Question 2.
Mr. A for his personal use is preferring to use which Computing Model?
(a) Cloud Computing
(b) Virtualization
(c) Grid Computing
(d) Green Computing
Answer:
(a) Cloud Computing
Question 3.
The XYZ University is using which Service Model of Cloud Computing?
(a) Platform as a Service
(b) Infrastructure as a Service
(c) Software as a Service
(d) Data as a Service
Answer:
(b) Infrastructure as a Service
Question 4.
“Reduce spending on technology infrastructure” is the advantage of
(a) Cloud Computing
(b) Virtualization
(c) Grid Computing
(d) Green Computing
Answer:
(a) Cloud Computing
Question 5.
This type of cloud are administrated by third parties or vendors over the Internet,
(a) Private
(b) Public
(c) Community
(d) Hybrid
Answer:
(b) Public
![]()
Question 6.
It is a private cloud is shared between several organizations.
(a) Public
(b) Community
(c) Hybrid
(d) None of the above
Answer:
(b) Community
Case Study 8
A bank XYZ has many branches all over India. They provide major products and services through its various branches. However, the competent authority intends to bring all the branches together under one umbrella and make it centralized.
Crosys is a leading Information technology company in India offering quality software products and services both in the domestic and international markets. The Bank has signed a strategic IT partnership with Crosys. Accordingly, XYZ Bank has licensed Prosys Banking software which includes Banksoft – the Core Banking Solution, eConnect – the Financial Middleware, and eBanker – the Internet Banking Solution. XYZ Bank intends to deploy Banksoft across 3000 branches over the next 2 years.
Based on the above case scenario, answer the following questions:
Question 1.
XYZ Bank should use which System?
(a) Main banking Solutions
(b) Core Banking Solutions
(c Non-Integrated System
(d) Oracle
Answer:
(b) Core Banking Solutions
Question 2.
Which one of the following is not an example of CBS Software?
(a) Finacle
(b) FinnOne
(c) Oracle
(d) BankMatc
Answer:
(c) Oracle
![]()
Question 3.
Branch Banking is a ___________
(a) Back End Applications
(b) Front End Applications
(c) Integrated Applications
(d) Non-Integrated Applications
Answer:
(b) Front End Applications
Question 4.
Which one of the following is not a Key Aspect in built into Architecture of CBS?
(a) Regulatory compliance
(b) Information Accuracy
(c) Resource optimization
(d) Customer centric
Answer:
(b) Information Accuracy
Question 5.
This Server performs necessary operations and this updates the account of the customer.
(a) Database Server
(b) Application Server
(c) Web Server
(d) Proxy Server
Answer:
(b) Application Server
![]()
Question 6.
A client connects to the __________ server, and then requests a connection, file, or other resource available on a different server.
(a) Database Server
(b) Application Server
(c) Web Server
(d) Proxy Server
Answer:
(d) Proxy Server