Automated Business Process – CA Inter EIS Notes is designed strictly as per the latest syllabus and exam pattern.
Automated Business Process – CA Inter EIS Study Material
Question 1.
In Organization Business processes, what is the difference between Operational processes, Supporting processes and Management processes? Give examples.
Answer:
- OPERATIONAL PROCESSES (OR PRIMARY PROCESSES)
- Operational Processes deal with the essential business and value chain,
- They deliver and bring value to the customer by serving to produce a product or service.
- They signify important business activities that achieve business objectives.
- Example are: Revenue Generation – Order to Cash cycle, Procurement – Purchase to Pay cycle.
- SUPPORTING PROCESSES (OR SECONDARY PROCESSES)
- Supporting Processes support and back the essential processes and functions within organization.
- Examples are: Accounting, Human Resource (HR) Management and workplace safety.
- They do not deliver value to customers directly.
- It is important to note that hiring right people for right job improves efficiency of the Organization.
- MANAGEMENT PROCESSES
- They helps to not only measure, but also monitor and control activities which are related to business procedures and processes.
- Examples are: internal communications, governance, strategic planning, budgeting, infrastructure or capacity management.
- They also do not provide value directly to the customers; but has a direct effect on the efficiency of the Organization.
- Example: Budgeting should be determined by vision and strategic plan.
![]()
Question 2.
What are the Factors affecting BPA Success?
OR
What are the Objectives of BPA?
OR
Recognize the Parameters based on which the Success of BPA can be evaluated?
Answer:
Generally, Success of Business process automation can be achieved when BPA confirms and ensures the following:
- Confidentiality: To confirm that data is made available to individuals who have the authority and right to see;
- Integrity: To confirm that no unauthorized modifications can be made in the data;
- Availability: To confirm that data is made available when requested for; and
- Timeliness: To confirm that data is made available at the right time,
BPA needs to have appropriate internal controls put in place; so as to confirm that all the above parameters are met.
Question 3.
A travel agency ABC wishes to implement an automated Grievance Management System at its workplace to manage and handle the problems with an aim of solving them. Determine the major benefits that will be 1 drawn out of automating this Grievance related business process. (RTP May 2018)
A business organization is planning to increase the accuracy of information transferred and certifies the repeatability of the value added task performed by the automation of business. Being a management consultant, identify any four major benefits that the organization can achieve through the automation of a business process. (May 2019; 4 Marks)
Answer:
- Time Saving:
- Automation basically decreases number of manual tasks that employees might have to do.
- It provides free time to work on those items that increases genuine value to the business, and also allows innovation.
- Reduced Turnaround times:
- It helps to eradicate unnecessary tasks.
- Rearrange process steps so that the flow of information can be optimized throughout manufacturing, service, billing, etc.
- This adjustment of processes purifies operational performance and also helps to reduce turnaround times.
- Reduced Costs:
- Manual tasks generally cost more because they are performed one-at-a-time and at relatively slow speed as compared to Automation tasks,
- Automation helps to accomplish more by utilising less resources.
- Improved Operational Efficiency:
- Automation helps to reduce time taken to achieve a task, efforts required and the cost of completing task.
- Automation ensures that the errors are removed and the systems run smoothly and efficiently.
- Quality and Consistency:
Automation helps to Ensure that each action is performed in a similar way which brings high quality, reliable results. - Governance & Reliability
Stakeholders can trust on business processes operated with the help of automation and automation can offer reliable processes to customers, thus helps to maintain a competitive advantage. - Visibility:
- Automated processes operates accurately and consistently within the defined timeline.
- Automated Processes helps to give visibility of the process status to the organization.
![]()
Question 4.
An Airline Industry wishes to automate its Grievance cell so that their clients can online register their feedback, complaints and suggestions. The I purpose of automation is to provide better service and satisfaction to its customers. Prepare a list of various steps that are required to be taken while automating the Grievance Cell.
OR
Describe the steps to go about implementing Business process Automation.
Answer:
Steps that are required to automate the Grievance Cell of the Airline Industry are:
Step 1: Define why we plan to implement a Business Process Automation (BPA)?
The main purpose for which an Organization implements automation may ’ vary from Organization to Organization. In the given case, to improve upon j the Poor customer service is a major concern.
Step 2: Understand the rules/regulation under which Organization needs to comply with?
This step emphasizes on building an understanding on the rules of i engagement, which include following the rules, adhering to regulations and i following document retention requirements. This governance is established by a combination of internal corporate policies, external industry regulations and local, state, and central laws.
Step 3: Document the process, we wish to automate
At this step, all the documents that are currently being used need to be j documented.
The questions emphasized upon are like :
- What format are the documents are in?
- What documents should be captured?
- Where do they come from?
- Who is involved in processing of the documents?;
- How are exceptions in the process handled? etc.
- What is the impact of regulations on processing of these documents?
- Can there be a better way to do the same job? and
Step 4: Define the objectives/goals to be achieved by implementing BPA –
Organization needs to determine the key objectives of the process improvement activities.
The required characteristics of goals to be achieved by implementing Business Process Automation (BPA) could be abbreviated as “SMART” which means:
Specific: Clearly defined;
Measurable: Easily quantifiable in monetary terms;
Attainable: Achievable through best efforts;
Relevant: Entity must need these and I Timely: Achieved within a given time frame.
Step 5: Engage the business process consultant –
To decide as to which company/consultant to partner with, depends upon the following:
- Whether the consultant have experience with entity business process?
- Objective of consultant in understanding/evaluating entity situation.
- Whether the consultant experienced in resolving critical business issues?
- Whether the consultant have required expertise to clearly mention the business value of every aspect of the proposed solution?
- Can the consultant recommend and implement a combination of hardware, software and services as appropriate to meeting Organization BPA requirements?
Step 6: Calculate the Rol for project
The right stakeholders must be engaged and involved to ensure that benefits of BPA are communicated clearly and implementation becomes successful.
A lot of careful effort is required to persuade the senior management with respect to need to implement the appropriate solution for BPA.
Step 7: Developing the BPA
After the documentation of requirements, computation of ROI and approval of Top Management to go ahead has been received, the consultant develops the requisite BPA. The developed BPA needs to meet the objectives for which the same is being developed.
Step 8: Testing the BPA
After the development, it is important to test the new process to know how well it works and identify where additional “exception processing” steps ; are required to be included. The process of testing is a repetitive process, the objective is to eradicate all problems during this phase.
![]()
Question 5.
State the required characteristics of goals to be achieved by implementing Business Process Automation (BPA). (Nov 2018; 2 Marks)
Answer:
The required characteristics of goals to be achieved by implementing Business Process Automation (BPA) is abbreviated as “SMART” which means:
Specific: Defined precisely;
Measurable: Quanti1able in monetary terms;
Attainable: Achievable through best efforts;
Relevant: Entity required these, and
Timely: Achieved within a specific time.
![]()
Question 6.
Explain the different types of Business Risks?
OR
Businesses face all kinds of risks related from serious loss of profits to even bankruptcy. Describe in brief.
Answer:
Businesses face all kinds of risks related from serious loss of profits to even bankruptcy and are discussed below:
STRATEGIC RISK:
Strategic risks are the risks that would stop organization from achievement of its objectives (meeting its goals). Examples are: Risks related to strategy, political, economic, regulatory, and global market conditions; reputation risk, leadership risk, brand risk.
FINANCIAL RISK:
Financial Risk that may result in negative financial impact to the Entity (waste or loss of assets). Examples are: Risks from volatility in foreign currencies, interest rates, and commodities; credit risk, liquidity risk.
REGULATORY (COMPLIANCE) RISK:
Due to non-compliance with laws and regulations; Organization may get expose to penalties from regulatory agency. These are Regulatory X Risk. Examples: Violation of laws which govern areas such as environmental, employee health and safety, protection of personal data as per statutory laws, global data protection requirements.
OPERATIONAL RISK:
They are the risk that will prevent organization from operating in the effective and efficient manner. Examples are: Risks related to the failure of services and products; organization’s human resources, business processes, technology, business continuity, customer satisfaction, health and safety, environment.
HAZARD RISK:
Insurable risks such as natural disasters; various insurable liabilities; impairment of physical assets; terrorism etc are the Hazard risk.
RESIDUAL RISK:
Risk remaining after the counter measures are analyzed and implemented is called Residual Risk. Entity’s management of risk need to consider two areas: Acceptance of residual risk and Selection of safeguards. Even when safeguards are applied, there is probably going to be some residual risk. The risk can be minimized, but they cannot be eliminated. Therefore, we can say that Residual risk must be kept at a minimal, acceptable level.
![]()
Question 7.
Analyse new set of IT risks and challenges associated with the businesses and standards that the banks should consider? (RTP Nov. 2018)
Answer:
Dependence on technology in banking for most of the key banking services and processes has led to various challenges. The business processes and standards adapted by Banks need to consider these new set of IT risks and challenges:
(i) Frequent changes or obsolescence of technology: Technology keeps on growing and changing constantly and becomes outdated very quickly. Therefore, there is always a risk that the investment in technology solutions may result in loss to bank unless properly planned.
(ii) Different types of controls for different types of technologies/systems:
There comes new types of risks due to Deployment of Technology, Risks need to be reduced bv controls as applicable to the technology/ information systems deployed in the bank.
(iii) Multiplicity and Complexity of Systems:
Technology architecture which are used for services may include multiple digital platforms and it is complex. Therefore, this requires the bank employees to have employees with necessary technology skills or the management of the bank’s technology could be outsourced to a company having the relevant skill set.
(iv) Dependence on vendors due to outsourcing of IT services:
Organization requires staff with expertise domain skills to manage IT deployed. Therefore, such services can be outsourced to vendors. Since there would be heavy dependency on vendors and therefore it will give rise to vendor risks which should be managed by proper contracts, controls and monitoring.
(v) Vendor related concentration risk:
There can be multiple vendors providing different services. Certain situations result in higher risks due to heavy dependence on vendors. Example, network, hardware, system software and banking software services can be provided by different vendors. Also these services may be provided by a single vendor.
![]()
(vi) External threats leading to cyber frauds/crime:
Systems environment provides access to customers anytime, anywhere using internet. Therefore, information system which in past was accessible only within organization and to the employees is now getting exposed since it is open to be accessed by anyone from anywhere.
(vii) Segregation of Duties (SoD):
Segregation of duties as per structure needs to be clearly mapped in the CBS used by the bank. This is a high- risk area since any SoD conflicts can be a potential vulnerability for fraudulent activities. Organizations have a highly-defined organization structure with clearly defined roles, authority and responsibility. For example, if a single employee can initiate, authorize and disburse a loan the possibility of misuse cannot be ignored.
(viii) Higher impact due to intentional or unintentional acts of internal employees:
Employees in a technology environment are the weakest link in an Organization.
(ix) Proper alignment with business objectives and legal/regulatory requirements:
Organizations must ensure that the systems implemented, cater to all the business objectives and needs, in addition to the legal/ regulatory requirements envisaged.
(x) New social engineering techniques employed to acquire confidential credentials: Fraudsters use new social engineering techniques such as socializing with employees and extracting information which is used unauthorized to commit frauds. For example: extracting information about passwords from bank’s staff acting as genuine customer and using it to commit frauds.
(xi) Need for governance processes to adequately manage technology g and information security: Controls in System should be implemented § from macro and business perspective and not just from function and technology perspective.
(xii) Need to ensure continuity of business processes in the event of major exigencies: The high dependence on technology makes it compulsory to ensure resilience to ensure that failure does not impact banking services. Therefore, a documented business continuity plan with adequate technology and information systems should be planned, implemented and monitored.
![]()
Question 8.
Explain in brief Risk Management Strategies.
OR
In an organization, effective risk management involves identification of high-level risk exposures and their analysis. Discuss all the risk management strategies out of which Senior Management of an organization may choose to adopt any of the risk management strategy based on the analysis of risks. (RTP May 2020)
Answer:
When risks are identified, and analyzed, it is not always appropriate to implement controls to counter them. Some risks may be minor, and it may not be cost effective to implement expensive control processes for them. Risk management strategy is explained below:
- Tolerate/Accept the risk: Some risks may be considered minor since their impact and probability of occurrence is low. One of the primary functions of management is managing risk. In such case, intentionally accepting the risk as a cost of doing business is appropriate.
- Terminate/Eliminate the risk: Risk can be associated with the use of a technology, supplier, or vendor. The risk can be eradicated by replacing the technology with more vigorous products and by having more capable suppliers and vendors
- Transfer/Share the risk: Risk mitigation approaches may be shared with trading partners and suppliers. A good example is outsourcing infrastructure management. In such a case, the supplier reduces the risks associated with j managing the IT infrastructure by being more capable and having access to more highly skilled staff.
- Treat/mitigate the risk: Appropriate controls must be devised and implemented to prevent the risk from manifesting itself or to minimize its effects.
- Turn back: Where the probability or impact of the risk is very low, then management may decide to ignore the risk.
![]()
Question 9.
General controls are pervasive controls and apply to all systems components processes and data for a given Organization or systems environment. As an IT consultant, discuss some of the controls covered under general controls which you would like to ensure for a given Organization. (May 2019; 6 Marks)
Answer:
General Controls also known as Infrastructure Controls is present across different layers of IT environment and information systems and apply to all systems, components, processes, and data for a given Organization or systems environment.
General controls normally includes:
- Information Security Policy: It is approved by the senior management and includes all areas of operations of bank and drives access to information across the Organization.
- Administration, Access, and Authentication: IT should be managed and administered by proper policies and procedures clearly defining the levels of access to information and authentication.
- Separation of key IT functions: Entity need to ensure that there are no Segregation of Duties (SoD) conflicts. Secure deployment of IT requires the bank to have separate IT organization structure with key I differentiation of duties for different employees within IT department.
- Management of Systems Acquisition and Implementation: The process of acquisition and implementation of systems should be properly controlled and monitored.
- Change Management: IT solutions deployed and its various components must be changed according to the changing needs and as per changes in technology environment, business processes. Change management process should be implemented to ensure smooth transition to new environments.
- Backup, Recovery and Business Continuity: Heavy dependence on IT and criticality makes it crucial that resilience of banking operations need to be ensured by having appropriate business continuity including backup, recovery.
- Proper Development and Implementation of Application Software: Application software helps to run the business processes of the banks. These solutions developed and implemented must be appropriately controlled by using standard software development process.
- Confidentiality, Integrity and Availability of Software and data files: Security is implemented to ensure Confidentiality, Integrity and Availability of information. Confidentiality refers to protection of critical information. Integrity refers to ensuring authenticity of information at all stages of processing. Availability refers to ensuring availability of information to users when required.
- User training and qualification of Operations employees: Employees positioned have required competencies and skill-sets to work and monitor the IT environment.
- Incident response and management: Various incidents are created due to failure of IT. These incidents must be correctly responded and managed as per standard policies and procedures.
- Monitoring of Applications and supporting Servers: The Servers and applications running on them are monitored to ensure that servers, network connections and application software along with the interfaces are working continuously.
- Value Add areas of Service Level Agreements (SLA): SLA with vendors is regularly reviewed to ensure that the services are delivered as per specified performance parameters.
![]()
Question 10.
Explain in brief Application Controls.
Answer:
Application Controls
- Controls which are implemented within an application to prevent, detect and correct errors are called as Application Controls.
- Example: In Banking, application software ensures that only transactions of the day are accepted by the system.
- These controls are basically in-built within the application software to ensure accurate and reliable processing.
Examples of Application controls are as follows:- Transaction logging (all transactions are identified with unique id and logged);
- Data edits (only for permissible fields editing of data is allowed);
- Exception Reporting (all exceptions are reported here).
- Separation of business functions (e.g., transaction initiation versus authorization);
- Balancing of processing totals (debit and credit of all transactions are tallied);
- Error reporting (errors during the process are reported); and
Question 11.
What are the Key indicators of effective IT controls?
Answer:
- Higher security awareness on the part of the users & a culture of security consciousness withing organization.
- IT infrastructure upgrades are required to back new products and services, and ability is required to execute and plan new work.
- Development projects that are delivered on time and within budget, resulting in cost-effective and better product and service offerings compared to competitors.
- Ability to allocate resources in a predictable manner.
- Consistent availability and reliability of information and IT services across the organization and for customers, business partners, and other external interfaces.
- Clear communication to management of key indicators of effective controls.
- The ability to protect against new vulnerabilities and threats and to recover from any disruption of IT services quickly and efficiently.
- To make efficient use of a help desk or customer support center.
![]()
Question 12.
What are the Components of Internal Control?
Commercial Laws that are applicable to any E-Commerce or M-Commerce Transactions are as described below:
SA 315 explains the five components of any internal control as they relate to a financial statement audit. The five components are as follows:
Answer:
- CONTROL ENVIRONMENT:
- The Control Environment are basically the set of standards, processes, and structures which gives a base to carry out internal control across the organization.
- The board of directors and senior management set the tone at the top with respect to the importance of internal control, including expected standards of conduct.
- The control environment encompasses the integrity and ethical values of the organization.
- RISK ASSESSMENT (May 2018; 2 Marks)
- Every entity faces a variety of risks from external and internal resources.
- Risk can be defined as the possibility that an event will occur and unfavourably affect the accomplishment of objectives.
- Risk assessment involves a active and repetitive process for recognizing and assessing risks to the achievement of objectives.
- Thus, risk assessment becomes the base for determining how risks will be managed.
- CONTROL ACTIVITIES
- Control Activities are basically the actions established through policies and procedures.
- This helps to ensure that management’s directives to alleviate risks to the achievement of objectives are being implemented effectively.
- Control activities are performed at all levels of the entity, at various stages within business processes, and over the technology environment.
- Control activities include the elements that operate to ensure transactions are authorized, duties are segregated, adequate documents and records are maintained, assets and records are safeguarded, and | independent checks on performance and valuation of records.
- INFORMATION & COMMUNICATION
- Information is essential for the entity to implement internal control responsibilities in support of the achievement of its objectives.
- Management gets or produces and uses relevant and quality information from both internal and external sources.
- Communication is the continual, iterative process which helps to provide, share, and obtain necessary information.
- MONITORING OF CONTROLS
- One need to determine whether each of the five components of internal control, are present and functioning; with the help of ongoing evaluations, separate evaluations.
- Ongoing evaluations made into business processes at different levels of the entity, provide timely information.
- Separate evaluations, conducted periodically, will vary in scope and frequency.
![]()
Question 13.
What are the limitations of internal control system? (RTP May 2018)
Answer:
Internal control provide entity with reasonable assurance, absolute assurance to achieve the entity’s operational, financial reporting and compliance objectives.
Inherent limitations in Internal control systems are:
- Most internal controls do not incline to be directed at transactions of unusual nature. The potential for human error due to carelessness, distraction, errors of judgment and misunderstanding of instructions,
- There can be probability that a person who is responsible for exercising an internal control could misuse that responsibility. Example, a member of management overruling an internal control.
- Possibility of evasion of internal controls through collusion with employees or with parties outside the entity.
- Management’s contemplation that the expected benefits are more than cost of internal control.
- Manipulations made by management in relation to transactions, estimates and judgments which are required in preparing financial statements.
Question 14.
“Organization Risk Management (ERM) does not create a risk-free i environment; rather it enables management to operate more effectively in environments filled with risks”. In view of this statement, explain the various benefits, which Board of Directors and Management of an entity seek to achieve by implementing the ERM process within the entity, (Nov. 2018; 6 Marks)
Answer:
Entity operates in a risk-free environment, and ERM does not create such an environment. Rather, it enables management to operate more 5 effectively in environments filled with risks.
ERM provides enhanced capability to do the following:
1. Identify and manage cross-Organization risks: Every entity faces a innumerable risks which affect different parts of the Organization. Management should manage individual risks, and also understand the impacts which are inter-related.
2. Enhance risk response decisions: ERM provides strictness to identify and select among alternative risk responses – risk avoidance, reduction, sharing and acceptance. ERM provides methodologies and techniques which helps to make decisions.
3. Provide integrated responses to multiple risks: Business processes carry many inherent risks, and ERM enables unified solutions to manage the risks.
4. Minimize operational surprises and losses: Entities have greater capability to identify potential events, assess risk and establish responses, and accordingly reduce the occurrence of surprises and losses.
5. Seize opportunities: Management considers potential events, rather than just risks, and by considering a full range of events, management gains an understanding of how certain events represent opportunities.
6. Align risk appetite and strategy: Risk appetite is the degree of risk that Organization is willing to accept in pursuit of its goals. Management considers the entity’s risk appetite first in evaluating strategic alternatives, then in setting objectives aligned with the selected strategy and in developing mechanisms to manage the related risks.
7. Link growth, risk and return: Entities accept risk as part of value creation and preservation, and they expect return commensurate with the risk. ERM provides an enhanced ability to identify and assess risks, and establish acceptable levels of risk relative to growth and return objectives.
8. Rationalize capital: More robust information on an entity’s total risk allows management to more effectively assess overall capital needs and improve capital allocation.
![]()
Question 15.
ERM framework identifies risks and opportunities to protect the business and create the value for stakeholders, including owners, customer, regulators and society overall. Briefly explain all the components of ERM framework. (RTPNov. 2020)
OR
What are the Components of ERM?
Answer:
ERM framework consists of eight interrelated components that are j derived from the way management runs a business, and are integrated with the management process. These components are as follows:
- Internal Environment:
- The internal environment sets the tone of an organization, and the basis § for how risk is viewed and addressed by an entity’s people, including risk management philosophy and risk appetite, integrity and ethical) values, and the environment.
- Management sets a philosophy regarding risk and establishes a risk appetite i.e. degree of risk enterprise is willing to accept.
- Internal environment sets the foundation for how risk and control are viewed and addressed by an entity’s management and personnel.
- Risk Assessment:
- Identified risks are analyzed to form conclusion to determine how the should be managed and controlled.
- Risks arc associated with related objectives which can be affected.
- Risks are assessed on both an inherent & a residual basis.
- Control Activities:
- To confirm that risk responses which management have selected are carried out properly and effectively; policies and procedures are established and executed.
- Information and Communication:
- To carry out responsibilities properly and effectively; Relevant in-formation is identified, captured and communicated in a form and appropriate time frame.
- Information is required at all levels of an entity which helps in identifying, assessing and responding to risk.
- Employees should receive clear communications regarding their role and responsibilities, to carry out their work effectively.
- Monitoring:
- Entire ERM process should be monitored, and modifications need to be made as necessary.
- System can react dynamically, changing as conditions warrant,
- Monitoring is achieved by having ongoing management activities, separate evaluations of the ERM processes, or their combination.
- Objective Setting:
- Before management can identify events potentially affecting their achievement; Objectives should be set.
- ERM need to ensure that management has a process in place to set objectives.
- Selected objectives support and align with the entity’s mission/vision
- They need to be consistent with the organization’s risk appetite.
- Event Identification:
- Potential events that may have an effect on the organization should be identified.
- Identification of Events includes identifying factors (internal and external) which influence how potential events can affect strategy implementation and achievement of objectives.
- It includes distinguishing between potential events that represent risks, with those that represent opportunities and those that may be both.
- Risk Response:
- Management selects an approach to align assessed risks with the entity’s risk tolerance and risk appetite, within the context of the strategy and objectives.
- Employees then have to identify and evaluate possible responses to risks, including avoiding, accepting, reducing and sharing of risk.
![]()
Question 16.
Business Processes are documented/designed using flow-charts to understand the process in visualized form. Being a business advisor, what advantages of flow-charts will you suggest to represent the business processes in diagrammatic form? (Nov. 2019; 6 Marks)
Answer:
- Program Debugging-Flow-charts are an important tool during program debugging. Flow-charts helps in detecting, locating and removing any errors.
- Identifying Responsibilities – To establish responsibility of the Process owner, Specific business processes can be clearly identified to functional departments.
- Documentation-Flow-charts provides good documentation which help majorly in future program conversions. If staff changes, they serve as training function by helping the new employees to understand the existing programs.
- Communication – Flow-charts helps to communicate facts of a business problem to those whose skills are needed to arrive at the solution.
- Quicker grasp of relationships – The relationship between various elements of the application program/business process must be identified, Flow-chart may help to depict a lengthy and complex procedure more easily rather than by describing those procedures by means of written notes.
- Effective Analysis – Flowchart turn out to be a blue print of a system j that can be broken down into comprehensive parts for study. Problems may be identified and new approaches may be suggested by flowcharts.
- Efficient coding – Flowcharts provides guidance during the system analysis and program preparation phase. Instructions coded in a programming language may be checked against the flowchart which helps to ensure that no steps are omitted.
- Efficient program maintenance – Maintenance of operating programs are supported by flowcharts. Flowcharts helps programmer to focus on those part of the information flow which is to be modified.
- Establishing Controls – Business process conflicts and risks may be simply identified for to recommend suitable controls.
![]()
Question 17.
Explain ‘Data Flow Diagram’. (Nov. 2018; 2 Marks)
Answer:
- Data Flow Diagrams (DFD) displays the flow of data or information from one place to another.
- DFDs define the processes showing how these processes link together through data stores and how the processes relate to the users and the outside world.
- DFD basically provides an overview of:
- What transformations are performed;
- What does a system processes;
- What data are stored;
- What results are produced?
![]()
Question 18.
Explain the salient features of Section 134 & Section 143 of the Companies Act, 2013.
Answer:
Section 134 of the Companies Act, 2013 on “Financial statement, Board’s report, etc.” states:
The Directors’ Responsibility Statement shall state that:
- The Directors take proper and sufficient care:
- to safeguard the assets of the company,
- to maintain of adequate accounting records in accordance with the provisions of this Act,
- to prevent and detect fraud and other irregularities;
- The directors, in the case of a listed company:
- had laid down internal financial controls which is to be followed by the company and
- such internal financial controls are adequate and were operating effectively.
For the purposes of this clause, the term ‘Internal Financial Controls’ means: the policies and procedures adopted by the company for ensuring:
- the safeguarding of its assets,
- the accuracy and completeness of the accounting records,
- the prevention and detection of frauds and errors,
- the orderly and efficient conduct of its business, including adherence to company’s policies,
- and the timely preparation of reliable financial information
Section 143, of the Companies Act, 2013, on “Powers and duties of auditors and auditing standards” states inter alia:
Section 143(3) contains the auditor’s report which states:
‘whether the company has adequate internal financial controls system in place and the operating effectiveness of such controls’;
‘Adequacy and effectiveness of controls’ refers to the:
- adequacy of the control design and
- whether the control has been working effectively during the relevant financial year.
![]()
Question 19.
Corporate governance is the framework of rules and practices, by which a board of directors ensures accountability, fairness and transparency in a company’s relationship with all its stakeholders. List out the i rules and procedures that constitute corporate governance framework. (May 2019; 3 Marks)
Answer:
Corporate Governance is the framework of rules and practices.
With the help of Corporate Governance, Board of directors confirms accountability, fairness, and transparency in a company’s relationship with its all its respective stakeholders (Hnancers, customers, management, employees, government, and the community).
Corporate governance framework consists of:
- explicit and implicit contracts between the company and the stakeholders for distribution of responsibilities, rights, and rewards
- procedures for reconciling the conflicting interests of stakeholders in accordance with their duties, privileges, and roles, and
- procedures for proper supervision, control, and information-flows to serve as a system of checks-and-balances.
![]()
Question 20.
Explain the positive aspects contained in IT Act, 2000 and its provisions from the perspective of E-Commerce in India. (May 2018; 4 Marks)
Answer:
With respect to the perspective of e-commerce in India, the IT Act 2000 and its provisions contain many positive aspects which are as follows:
- Implications for the c-businesses is that email would now he a valid and legal form of communication in India that can be duly produced and approved in a court of law.
- Companies will now be able to carry out electronic commerce using the legal infrastructure provided by the Act.
- In the IT Act, Digital signatures are given legal validity and sanction.
- The Act introduce the entry of corporate companies in the business of becoming Certifying Authorities to issue Digital Signatures Certificates.
- The Act allows Government to issue notification on the web thus heralding c-governance.
- The Act permits the companies to file any form, application or any other document with any office, authority, body or agency owned or controlled by the appropriate Government in electronic form.
- The Act addresses the important issues of security, which are critical to the success of electronic transactions.
- Under the IT Act 2000, it is possible for Corporates to have a statutory remedy in case if anyone breaks into their computer systems or net work and causes damages or copies data. The remedy provided by the Act is in the form of monetary damages, not exceeding ₹ crore
- The Act has given a legal definition to the concept of secure digital signatures that is required to have been passed through a system of a security procedure, as stipulated by the Government.
![]()
Question 21.
Though Human Resource (HR) Department plays an important role in development of any Organization, yet it has certain risks associated at every stage of its life cycle. Describe all the risks related to Human-Resource Department. (RTP May 2020)
Answer:
The risks associated with Human Resource Department are as given below:
(a) New employees are not added to the payroll master files.
(b) Terminated employees are not removed from the payroll master files.
(c) Employees are terminated without following statutory requirements.
(d) Employees who have left the company continue to have system access,
(e) Employees have system access in excess of their job requirements.
(f) Deletions from the payroll master files do not represent valid terminations.
(g) Invalid changes are made to the payroll master files.
(h) Changes to the payroll master files are not accurate.
(z) Changes to the payroll master files are not processed in a timely manner.
(j) Payroll master file data is not up to date.
(k) Additions to the payroll master files do not represent valid employees.
(l) Payroll is disbursed to inappropriate employees.
(m) System access to process employee master changes has not been restricted to the authorized users.
![]()
Question 22.
Give two examples each of the Risk and Control Objectives for the following business process:
Procure to Pay
Answer:
TABLE: RISKS AND CONTROL OBJECTIVES (MASTERS-P2P)
| Risk | Control Objective |
| Unauthorized changes to supplier master file. | Only valid changes are made to the supplier master file. |
| All valid changes to the supplier master file are not input and processed. | All valid changes to the supplier master file are input and processed. |
| Changes to the supplier master file are not correct. | Change to the supplier master file are Accurate. |
| Changes to the supplier master file are delayed & not processed in a timely manner. | Changes to the supplier master tile are processed in a timely manner. |
Transactions
Risks And Control Objectives (Transactions-P2p)
| Risk | Control Objective |
| Unauthorized purchase requisitions are ordered. | Purchase orders are placed only for approved requisitions. |
| Purchase orders are not entered correctly in the system. | Purchase orders are accurately entered. |
| Purchase orders issued are not input and processed. | All purchase orders issued are input and processed. |
| Amounts are posted in accounts payable for goods or services not received. | Amounts posted to accounts payable represent goods or services received. |
| Amounts posted to accounts payable are not properly calculated and recorded. | Accounts payable amounts are accurately calculated and recorded. |
| Amounts for goods or services received are not input and processed in accounts payable. | All amounts for goods or services received are input and processed to accounts payable. |
| Amounts for goods or services received are recorded in the wrong period. | Amounts for goods or services received are recorded in the appropriate period. |
| Accounts payable amounts are adjusted based on unacceptable reasons. | Accounts payable are adjusted only for valid reasons. |
![]()
Question 23.
Give two examples of the Risks and Control objectives for Human Resource Process at configuration level. (Nov. 2618; 2 Marks)
Answer:
| Risk | Control Objective |
| Employees who have left the company continue to have system access. | System access to be immediately removed when employees leave the company. |
| Employees have system access in excess of their job requirements. | Employees should be given system access based on a ‘need to know’ basis and to perform their job function. |
Question 24.
During a job interview , an interviewer asked Mr. A to list out ail the risks and their controls associated with Order-To-Cash (02C) business process. Prepare an appropriate draft reply. (RTP Nov. 2018)
Answer:
MASTERS
TABLE 1.8.3: RISKS AND CONTROL OBJECTIVES (MASTERS-02C)
| Risks | Controls |
| The customer master file is not maintained properly and the information is not accurate.
Invalid changes are made to the customer master file. All valid changes to the customer master file are not input and processed. Changes to the customer master file are not accurate. Changes to the customer master file are not processed in a timely manner. Customer master file data is not up-to- date and relevant. System access to maintain customer masters has not been restricted to the authorized users. |
The customer master file is maintained properly and the information is accurate.
Only valid changes are made to the customer master file. All valid changes to the customer master file are input and processed. Changes to the customer master file are accurate. Changes to the customer master file are processed in a timely manner. Customer master file data is up to date and relevant. System access to maintain customer masters has been restricted to the authorized users. |
![]()
Transactions
TABLE 1.8.4: RISKS AND CONTROL OBJECTIVES (TRANSACTI0NS-02C)
| Risk | Control Objective |
| Orders are processed exceeding customer credit limits without approvals. | Orders are processed only within approved customer credit limits. |
| Orders are not approved by management as to prices and terms of sale. | Orders are approved by management as to prices and terms of sale. |
| Orders and cancellations of orders are not input accurately. | Orders and cancellations of orders are input accurately. |
| Order entry data are not transferred completely and accurately to the shipping and invoicing activities. | Order entry data are transferred completely and accurately to the shipping and invoicing activities. |
| All orders received from customers are not input and processed. | All orders received from customers are input and processed. |
| Invalid & unauthorized orders are input and processed. | Only valid & authorized orders are input and processed. |
| Invoices are generated using unauthorized terms and prices. | Invoices are generated using authorized terms and prices. |
| Invoices are not accurately calculated and recorded. | Invoices are accurately calculated and recorded. |
![]()
Question 25.
Give five examples of computer related offences that can be prosecuted under the IT Act, 2000.
Answer:
1. Web Defacement
The homepage of a website is replaced with a pornographic or defam-atory page. Government sites generally face the wrath of hackers on symbolic days.
2. Phishing and Email Scams
Phishing involves fraudulently acquiring sensitive information through masquerading (Pretend to be something else) a site as a trusted entity (e.g. Passwords, credit card information).
3. Introducing Viruses, Worms, Backdoors, Rootkits, Trojans, Bugs
All of the above are some sort of malicious programs which are used to destroy or gain access to some electronic information.
4. Email Account Hacking
If victim’s email account is hacked and obscene emails are sent to people in victim’s address book.
5. Theft of Confidential Information
Many business organizations store their confidential information in computer systems. This information is targeted by rivals, criminals & disgruntled employees. (Disgruntled means disappointed)
6. Credit Card Fraud
Unsuspecting victims would use infected computers to make online transactions.
7. Harassment via fake public profile on social networking site
A fake profile of a person is created on a social networking site with the correct address, residential information or contact details but he/ she is labelled as ‘prostitute’ or a person of loose character’. This leads to harassment of the victim.
8. Online sale of illegal Articles
Where sale of narcotics, drugs weapons and wildlife is facilitated by the Internet.
9. Cyber Pornography
Among the largest businesses on Internet, pornography may not be illegal in many countries, but child pornography is.
10. Cyber Terrorism
Many terrorists use virtual (Drive, FTP sites) and physical storage- media (USB’s, hard drives) for hiding ini on nation and records of their illicit business.
11. Source Code Theft
A Source code generally is the most coveted and important ‘crown jewel’ asset of a company.
(Coveted means ‘Greatly desired’. Crown Jewel means ‘Valuable or Prized asset’
![]()
Important Flowcharts;
Question 26.
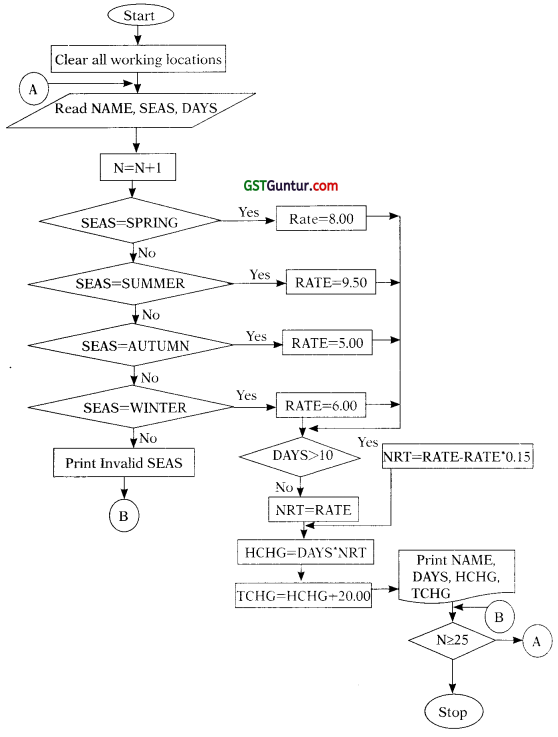
A bicycle shop in Delhi provides hired bicycles for day(s) at different rates as shown in table:
Season: – Charges Per Day
SPRING (MARCH-MAY): – ₹ 8.00
SUMMER (JUNE-AUG.): – ₹ 9.50
AUTUMN (SEPT-NOV.): – ₹ 5.00
WINTER (DEC.-FER): – ₹ 6.00
To attract his customers, the proprietor also gives a discount on the number of days a bicycle is hired for. If the hire period Is more than 10 days, a reduction of 15% is made. For every bicycle hired, a deposit of ₹ 20 must be paid.
Develop a flowchart to print out the details for each customer such as name of customer, number of days a bicycle is hired for, hire-charges and total charges including the deposit. It is also assumed that there are 25 customers and complete details for each customer such as name of customer, season and number of days the bicycle is required for is inputted through console, (RTP May 2018)
Answer:
Let us define the variables first:
NAME: Name of the customer
SEAS: Season in which bicycle is hired
DAYS: Number of days a bicycle is hired for
RATE: Hire charges of bicycle per day
N: Number of customers
NRT: Net Rate
HCHG: Hire Charges
TCHG: Total Charges
The required flowchart is shown below:
![]()
Question 27.
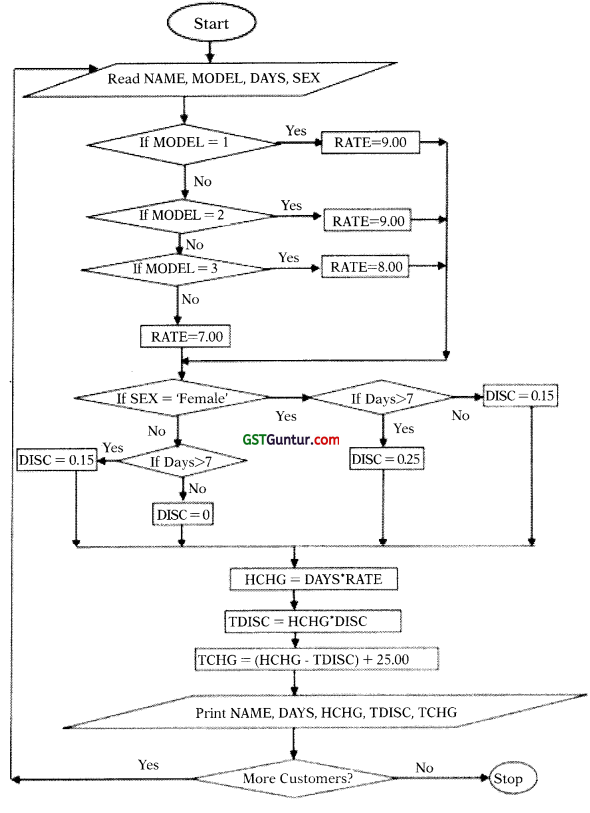
A bicycle shop in a city provides rental facility to Its customers at different rates for different models as given below:
| Model No. | Hire rate per day |
| Model No. 1 | ₹ 10 |
| Model No. 2 | ₹ 9 |
| Model No. 3 | ₹ 8 |
| Model No. 4 | ₹ 7 |
To attract customers, the shopkeeper gives a discount of 15 per cent to all those customers, who hire a bicycle for more than one-week period. Further to attract women customer, he gives additional discount of 10 per cent Irrespective of hire period. For every bicycle hired, a security deposit of ₹ 25 must be paid.
Draw a flow chart to print out the details of each customer such as name of customer, bicycle model number, number of days a bicycle is hired for, hire charges, discount and total charges including deposits. (RTPNov. 2018)
Answer:
Abbreviation used area as follows:
HCHG : Hire Charges
NAME : Name of customer
MODEL : Bicycle Model No.
SEX : Gender of the customer
DAYS : No. of days a bicycle is hired for
TCHG : Total Charges
TDISC : Total Discount
![]()
Question 28.
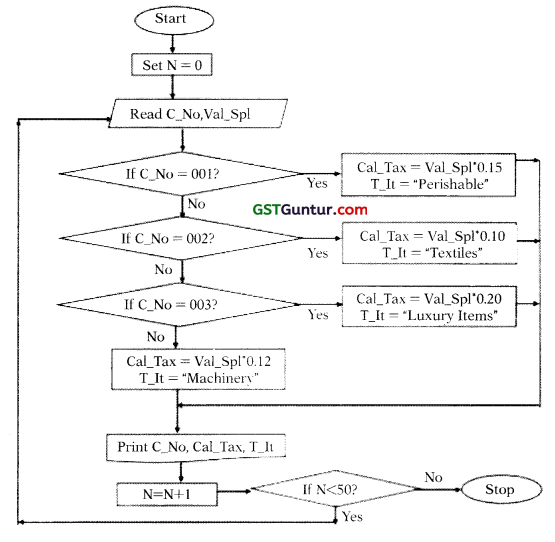
The GST of 50 items is to be calculated as per the following details. With Code No. and Value of Supply as input, draw a flowchart to calculate the Tax and print the Tax, Code No. of the Item and the Type of Item. (Note: The rates have been taken hypothetically) (RTP May 2019)
| Code No. (C _No.) | Types of Items | Tax Rate |
| 001 | Perishable | 15% |
| 002 | Textiles | 10% |
| 003 | Luxury Items | 20% |
| 004 | Machinery | 12% |
Answer:
The variables are defined as follows:
C = Code No;
Val_Spl = Value of Supply;
T_It = Types of Item
N = Counter;
Cal_Tax = Calculated Tax after GST
The required flowchart is as below:
![]()
Question 29.
A book publisher offered discount to customers based on their mode of purchase and the number of copies ordered as shown below:
| Mode of Purchase | Number of copies ordered | Discount% |
| Online | More than 5 | 20 |
| Less than or equal to 5 | 15 | |
| Offline | More than 10 | 10 |
| Less than or equal to 10 | 5 |
If Customer name, Customer typer Date of order placed, Number of copies ordered and unit price arc Input; draw a flowchart to calculate the net amount of the bill and date of purchase for each customer and print it.
The above is to be carried out for 50 customers. (RTP Nov. 2019)
Answer:
The required flowchart is given below:
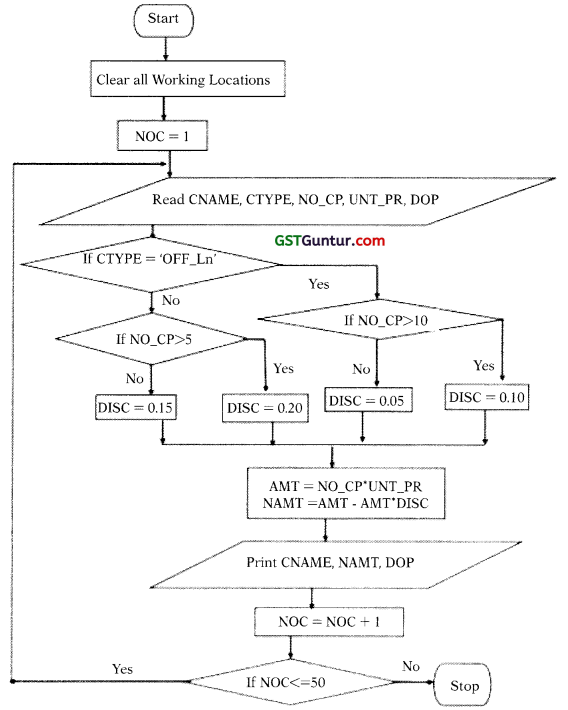
Abbreviations used in the flowchart are as follows:
DOP – Date of order placed
CNAME – Customer Name
NO_CP – Number of Copies
UNT_PR – Unit Price
DISC – Discount
AMT – Total Amount
NAMT – Net Amount
NOC – Number of Customers
CTYPE – Type of the Customer (Can either be Online or Offline[OFF_LN])
![]()
Question 30.
An e-commerce website is offering following discounts:
- If the purchase mode is via website, a discount of 5% is given on the bill amount.
- If the purchase mode is via phone app, a discount of 10% is given on bill amount.
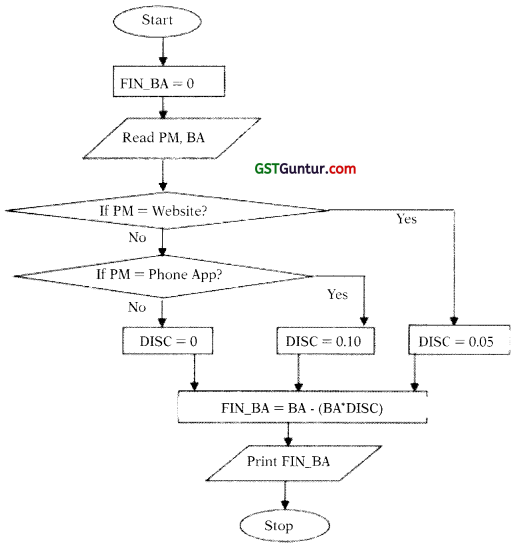
- If purchase is done via any other mode, customer is not eligible for any discount.
Draw a Flowchart to calculate and display the bill amount payable by the customer. (May 2018; 6 Marks)
Answer:
Let us define the variables first:
PM: Purchases Mode
BA: Bill Amount
FIN_BA: Final Bill Amount
DISC: Dicount